Recently, Microsoft announced a zero-day vulnerability in IE’s ActiveX video control, that required folks to react quickly to prevent exploits of this vulnerability. One of the possible routes for preventing this was to disable the affected ActiveX control in IE using so-called "Killbits" in the registry. This technique is described in general within a Microsoft KB article and specifically for this vulnerability within this document. Essentially, Killbits are a set of registry entries that must be enabled on a per-computer basis (i.e. within HKEY_LOCAL_MACHINE in the registry) that sets a flag on the GUIDs related to the given ActiveX Control. In the case of the recent video control vulnerability, there were something like 45 GUIDs requiring registry updates.
Someone asked me yesterday if Group Policy might not be a good way to push out these kinds of Killbits changes. And, not surprisingly, my answer was a solid, "YES!". Centralized registry change control, is, after all, the bread and butter of Group Policy for many enterprises. In this case, there are really two ways to skin this using Group Policy. The most obvious way is to create a custom ADM file (or ADMX for Vista/2008 environments) that hard codes the registry values in question. You can then add that ADM to a GPO in your AD environment and use it to target computer objects in AD for delivery of the Killbits values. Of course, the downside to that approach is that for any new ActiveX vulnerability that comes along, you have to create a new/modified ADM file with the new GUIDs.
Probably the easier way to handle this is to leverage our good friend, the Group Policy Preferences (GPP) feature that Microsoft introduced with Server 2008. Remember that you don’t need to have Server 2008 running in your environment to use GPP, but just need to have deployed the GPP Client Side Extensions (CSEs) to your XP, Vista and 2003 systems, and then you just need one Vista, SP1 or Server 2008 machine with GPMC installed to create and manage GPP settings. GPP includes a Registry extension (under either Computer or User ConfigurationPreferencesWindows SettingsRegistry) that lets you deploy "free-form" registry settings. One of the cool features of this Registry extension is the "Registry Wizard". The Wizard is designed to let you pick a bunch of existing registry values from the registry on a local or remote machine, and those are captured into policy without you having to manually enter anything! So, for example, you could apply the KillBits "Fix-it" package that Microsoft typically provides, to a test machine, and then use the Registry Wizard to capture those into a GPO, and push them out to all of your desktop machines. The following screen-shot shows an example of how this works with GPP and the Registry Wizard:
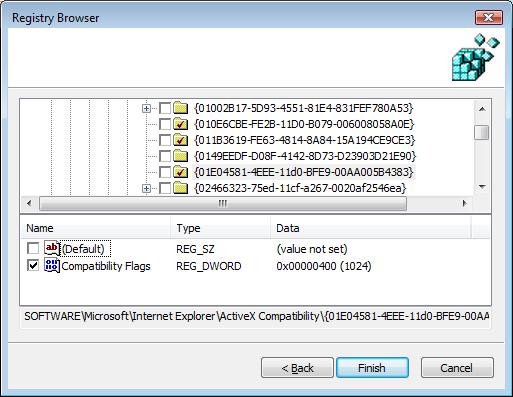
When you use the registry wizard in GPP to capture these registry entries, they are defined with a GPP Action type of "Update". This means that if these registry values exist already, they will be modified to conform to the KillBits value you specify. If they don’t exist, they will be created.
GPP provides a great mechanism for managing ActiveX Killbits settings, because they are centrally visible and manageable within the GP UI and you can use Group Policy’s built-in targeting mechanisms and even the more granular GPP Item-Level Targeting, to make sure all of the machines on your network receive the settings.
And of course, if you need to be able to automate reading or writing of these GPP Killbits registry settings, you can do that very easily with our GPExpert(r) Group Policy Automation Engine and Powershell!
Tags


