Over this last weekend, Microsoft published warnings of yet another zero-day “memory corruption” Internet Explorer vulnerability to all versions of the venerable browser . Since there is no current patch for this yet, IT administrators are left to mitigate against it using a variety of less than ideal workarounds, which are documented here. If you scan this article, you will notice that many of the workarounds can be deployed using our friend, Group Policy. Notably, this one:
“Configure Internet Explorer to prompt before running Active Scripting or to disable Active Scripting in the Internet and Local intranet security zone”
And this one:
“Add sites that you trust to the Internet Explorer Trusted sites zone”
Both of these options can be configured using either Administrative Templates or GP Preferences. With the first one, you will find the relevant Group Policy under “User Configuration\Policies\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page\Internet Zone (and/or Intranet Zone)\Allow Active Scripting. Once enabled, this policy can be set Enable, Disable or Prompt–the latter two options are the recommended value by Microsoft. Note that when you set this policy here, the user will not be able to change it.
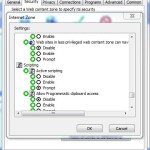
Conversely, if you decide to set this policy using GP Preferences Internet Settings, as shown below, the user can change the setting unless you lock down the security tab on IE using Admin Template settings.
The second part of this Microsoft recommendation, assigning sites you do trust to the trusted sites zone, can be managed using the “Site-to-zone Assignment” policy so that those sites are not subject to the active scripting limitations you’ve just imposed. This policy can be found under “User Configuration\Policies\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page\Site to Zone Assignment List”, but again, the user will not be able to add/remove any sites from the trusted sites list once this is done. The alternative in GP Preferences is not altogether straightforward, but was described well by my fellow Group Policy MVP Alan Burchill.
The next question becomes, “how do I roll these out across many GPOs or even local GPOs in an efficient manner?” This is where our (SDM Software’s) Group Policy Automation Engine (GPAE) comes in handy. If you’re not familiar with GPAE, it’s essentially a Group Policy SDK, exposed through either PowerShell or .Net, that allows you to read and write settings into GPOs. Enabling the settings above can be done against either domain-based GPOs or the local GPO on a bunch of remote systems, using a fairly simple script. Notably, the following PowerShell script sets Active Scripting in the Internet Zone to “Prompt” using Admin Templates and then enables a Site-to-zone-assignment that makes sdmsoftware.com a trusted site–all within a domain-based GPO:
[codebox lang=”ps”]
$gpo = Get-SDMgpobject “gpo://cpandl.com/IEVulnWorkaround Policy” -openbyname
#set Allow active scripting to Prompt
$container = $gpo.GetObject(“User Configuration/Administrative Templates/Windows Components/Internet Explorer/Internet Control Panel/Security Page/Internet Zone”)
$setting = $container.GetObject(“Allow active scripting”)
$setting.Put(“State”, [GPOSDK.AdmTempSettingState]”Enabled”)
$setting.Put(“Allow active scripting”,1)
$setting.Save()
#now add sdmsoftware.com to trusted sites list using site-to-zone-assignment
$setting = $gpo.GetObject(“User Configuration/Administrative Templates/Windows Components/Internet Explorer/Internet Control Panel/Security Page/Site to Zone Assignment List”)
$setting.Put(“State”,[GPOSDK.AdmTempSettingState]”Enabled”)
#add new site
$sites = @(“www.sdmsoftware.com”)
$setting.PutEx([GPOSDK.PropOp]”PROPERTY_UPDATE”,”Enter the zone assignments here._KEYS”,$sites)
#add value corresponding to the site
$values = @(“2″)
$setting.PutEx([GPOSDK.PropOp]”PROPERTY_UPDATE”,”Enter the zone assignments here.”,$values)
$setting.Save()
[/codebox]
As you can see, the first part of the script, lines 1-7, enables the “allow active scripting” policy with a value of 1 (Prompt). The rest of the script adds sdmsoftware.com as a Trusted Sites, thereby exempting it from the active scripting prompts. All of this can be scripted to work against multiple GPOs (or local GPOs) using tried and true PowerShell looping. If you’re interested in learning more about GPAE, visit the site link above to get a trial version!
Darren