This is my 2nd blog post around using the PowerShell features in the two products of SDM Software’s GPO Reporting Pak. In this post, I’ll talk about the GPO Exporter product, which, as the name implies, lets you export Group Policy settings. The cool thing about the tool is that you can tell it to export all settings across all GPOs in your domain into a single list. You can then sort that list to find GPOs that have potentially conflicting settings (i.e. different values for the same policy item). Before the Exporter, it was nearly impossible to do this in native tools without a lot of manual trolling through settings reports. In a recent update of GPO Exporter, we added a handy parameter to the Export-SDMGPSettings cmdlet called All. The -All parameter lets you tell the cmdlet to export all GPOs in the current (or specified domain), like so:
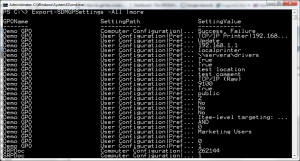
Export-SDMGPSettings -All
The output of the cmdlet is a custom object that lists all of the settings found, as shown here:
The custom object contains the name of the GPO, the path to the policy setting and the value. Using PowerShell, we have lots of options for manipulating this information in powerful ways, including the ability to find conflicting settings across all of my GPOs. Let’s say, for example, that we want to find all of the GPOs that contain the “Access this Computer from the Network” user rights assignment. Using PowerShell, GPO Exporter and the pipeline, we can accomplish this with relative ease as follows:
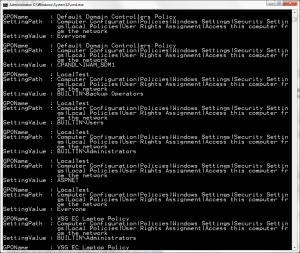
Export-SDMGPSettings -all | where {$_.SettingPath -like “*Access this computer from the network*”}
What this command is doing is exporting all GPO settings in my current domain and then piping that to a PowerShell where clause, where I look for any SettingPath values that include the string “Access this computer from the network”. The -like operator and the wildcard * before/after the string allow me to find this string within any part of the setting path. The output of this command looks like that shown here:
As you can see in this listing, it becomes much easier to find conflicting settings when you can see exactly which GPO(s) contain a particular setting.
Another cool by-product of this cmdlet is the ability to find references to, for example, security groups, across your GPOs. Let’s say for example, that you plan on retiring a particular security group and you want to find any and all settings that reference that group. That’s pretty hard to do through the UI, but PowerShell makes it a snap! The following command accomplishes my task:
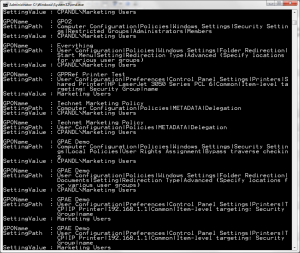
Export-SDMGPSettings -all -metadata | where {$_.SettingValue -like “*Marketing Users*”} |fl
You’ll notice this command looks very similar to the previous one except that I included the -metadata parameter on the GPO Exporter cmdlet, telling it to include metadata associated with GPOs (such as security group filtering). The cool part about this, is that it found instances of the Marketing Users group across security group filters, Restricted Groups policy, Folder Redirection policy and even GP Preferences item-level targeting by group! See below:
Now that’s some power!
Darren



The link to GPO Explorer above has changed. It’s now https://sdmsoftwarenew.wpengine.com/group-policy-management-products/group-policy-reporting-pak/