Recently I’ve had some conversations with folks that related to their irritation that “legacy” Group Policy settings such as Admin. Templates, Security Settings, Software Installation, etc. could not benefit from the fine-grained “Item-Level-Targeting” (ILT) feature that is available with Group Policy Preferences settings. Most of us Group Policy MVPs have had this on our wish list for a while, and, understanding GP structure and internals the way I do, I realized that this would not be an easy fix for Microsoft to undertake. However, as a thought exercise, I sat down and came up with a way to achieve this basic goal with the existing technology. It might be considered a bit of a “hack”, and does introduce a bit more complexity, but if you are really looking for this capability for a particular use case, I frankly think it’s not a bad solution! So, here’s what I did:
My test scenario was as follows. I wanted to deliver some Restricted Groups policy to a test Win7 machine. This policy would simply add the “GPO Admins” AD global group to the local “Administrators” group on my test machines. I created two GPOs for this test. The first one, called RestrictedGroups-Test, delivered the restricted groups policy. It was linked to my test OU, which contained a Win7 and XP system. It also had a WMI Filter associated with it, with the following filter query:
Select * from Win32_Environment WHERE Name=’ILT1′ AND VariableValue=’FileWin7′
This filter tested for an environment variable on the target system called ILT1 and for it to have a value of “FileWin7”
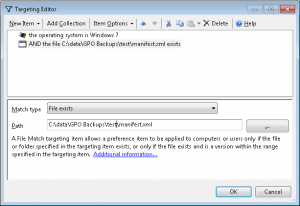
I had 2nd GPO, also linked to the same test OU. This GPO contained a single setting– a GP Preferences per-computer Environment variable setting that delivered–you guessed it–and environment variable called ILT1, if it met the ILT filter attached to that setting, which is shown below:
This ILT filter shown above is testing that the OS is Windows 7 and that there is a particular file present on that system in a particular path. But frankly, it could have been any ILT that tested for a up to 26 different criteria supported by ILT. The point is that if the system that processes this GPO meets the ILT criteria, an environment variable called “ILT1” will be created on the system with its value set to “FileWin7”. Once this environment variable is in place, then the RestrictedGroups-Test GPO, with it’s WMI filter looking for this environment variable, will pass once it applies and deliver the restricted groups settings. And, when it gets to my XP machine, it will simply fail to find that environment variable and will not apply.
And indeed, when I tested this, it worked as expected–the Win7 machine got the restricted groups policy and the XP machine did not. In your case, you might have to wait for a 2nd Group Policy update for the restricted groups policy to apply, because the first time through, the environment variable needs to created before the restricted groups policy can apply. However, in my testing, I linked the GPO with the ILT filter higher in precedence than the restricted groups GPO on the OU and it appeared that the ILT filter and environment variable processed first and then the restricted group policy was applied within the same cycle, so that was good!
So you might be asking at this point–why go to all this trouble to get ILT for “legacy” policy? Well, there are some things that ILT supports that are difficult to impossible to do with WMI filters. What I just did in this example scenario–testing for both OS and the presence of a particular file, can be challenging in WMI and, in the case of looking for a file, downright painful.
But this approach essentially proxies the ILT testing process into the environment variable, which is something that is easy to get at with WMI filters. You could imagine creating an “ILT GPO” that contains different named sets of test criteria that you’d like to use, and delivering different environment variables for each test criteria. And then, you can use those environment variables within your legacy GPOs to indirectly take advantage of ILT filtering!
Well, that’s today’s Epiphany Hack for Group Policy!
Would love to hear about folks that use this successfully! We’ll call it “gpoguy filtering” 🙂
Darren


YES, GP CAN! 🙂
Absolutly brilliant.
Very clever!
Excellent extraction of key technical bits from two areas to provide a cool solution.
Another use of ILT is self-triggering (or ‘self-detection’). At one point in time we were deploying PowerShell v1 to our Windows Server 2003 systems. We needed to make sure that all existing and future PowerShell Event logs were going to be at least 40 MB. The easiest solution was to pre-create the ‘MaxSize’ registry key (HKLM\SYSTEM\CurrentControlSet\Services\Eventlog\Windows PowerShell\MaxSize).
Here’s the problem: When you create that key, the Windows Event Log system automatically creates the rest of the necessary event keys in that hive and this creates a ‘false’ PowerShell event log that can be seen in the Event Log console. We knew that many hundreds of server admins would see the new ‘false’ event log and cry “Foul, we’ve not installed PowerShell” or worse “Who installed PoSH on my server?”
We needed find a way to have the Registry Preference wait until PowerShell was actually installed before configuring the event log registry keys. We chose to have the Registry Preference use Item Level Targeting to look for the existence of the same registry key whose value we wanted to control (the key would only appear once PowerShell was installed) and only then control the value of the key. In short, control the value of the MaxSize key ‘only after’ the MaxSize actually appears on the system. ILT: Registry Match: Value Exists: On the registry key noted above. Voila….
Jerry
Hi, Darren.
“I linked the GPO with the ILT filter higher in precedence than the restricted groups GPO on the OU and it appeared that the ILT filter and environment variable processed first and then the restricted group policy was applied within the same cycle, so that was good!”
The main point here is NOT the precedence, but the CSE processing order. Mark has a complete table of CSEs in their order on his web site: https://www.gruppenrichtlinien.de/Grundlagen/Client_Side_Extensions.htm
That has to be combined with the group policy evaluation process as found in https://technet.microsoft.com/en-us/library/cc784268%28WS.10%29.aspx (“GPO List creation”).
Anyway – ILT is cool 🙂 Especially the “store in variable” feature.
sincerely, Martin
Yep, thanks Martin. I’m aware of CSE order for sure. I left it out of this discussion but you’re absolutely right. The main point here is that the environment variable has to be there before the filter will work!