With RSA Conference going on this week here in San Francisco, I thought it was timely to talk about Group Policy’s role in securing your Windows environment. Many of you are undoubtedly using Group Policy to deliver security settings, based on industry-standard benchmarks from organizations like CIS or government standards like DISA-STIG. And through that process, how many times have you gotten an email or call from the boss or an auditor asking you to show him or her a report that proves that some particular security hardening setting (or group of settings) is actually in place on all of your Windows desktops or servers? I know from experience that it’s a tough problem to solve in any reasonable amount of time, in a decent sized Windows environment.
Sure, you can use PowerShell and run Get-GPResultantSetofPolicy against a system to get a GP results report from that system and parse through the results using XML. But due to some quirks in the implementation of that cmdlet, it’s a laborious process. You have to first generate an XML report using the cmdlet above, then cast that report document as XML so that you can navigate through it using PowerShell, like this screenshot below. I first generate the RSOP report, then convert it to XML in PowerShell, then navigate to the spot in the namespace where my setting lives, then try to decipher what the SettingValue actually corresponds to (in this case, for Advanced Audit Policy):
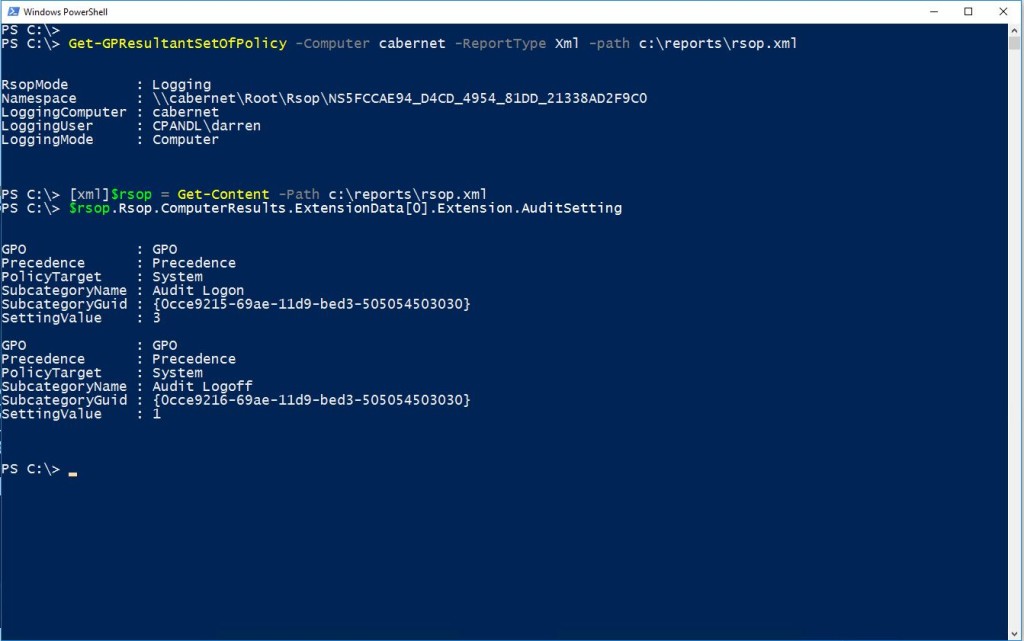
Using PowerShell to parse RSOP Settings
And this is for one system. Imagine having to do that across multiple systems and for multiple settings? Not fun. But there is a better way…
Group Policy Compliance Manager To The Rescue
The good news is that you don’t need to go through that painful process at all. That is where our Group Policy Compliance Manager (GPCM) product shines. GPCM has the ability to collect RSOP settings data from your entire environment. Once the data is collected, you can address all kinds of interesting reporting scenarios, including that one your boss is asking you for.
Let’s take our scenario from above–namely that I need to tell my boss which systems have received a particular security setting (and which have not). For our example, I’ll use the setting to control credential caching on Windows systems, namely this one:
Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security Options\Interactive logon: Number of previous logons to cache (in case domain controller is not available)
Your boss wants to know if the new setting, reducing this policy from the default 10 cached logons, to 7, is actually in place. How would you answer that for him?
Group Policy Compliance Manager’s PowerShell module has the answer. With the GPCM PowerShell module, you can ask a question like this and get a quick answer, using the Compare-SDMSettingBaseline cmdlet. This cmdlet queries the GPCM’s database of collected Group Policy settings data and returns not only the machines that received the policy, but also, which ones didn’t and which ones are different from the baseline–in this example, 7 logons. Let’s see how it works.
The following command line returns the data we’re after for my whole domain (I could also scope it to particular OUs):
Compare-SDMSettingBaseline -SettingPath "Computer Configuration|Policies|Windows Settings|Security Settings|Local Policies|Security Options|Interactive logon: Number of previous logons to cache (in case domain controller is not avaiable)" -SettingValue "7 logons" -UseSQL "SQLServer1" -Same
This command returns the list of machines in my domain that either contain the setting as it’s supposed to be set, are missing the setting completely, or have the setting but it’s not at the correct value. I can also filter the results using PowerShell’s where-object cmdlet, so that I only see machines that have different setting values or missing setting values or I can display the results in a grid view, by piping the results to the out-gridview cmdlet, as shown here:
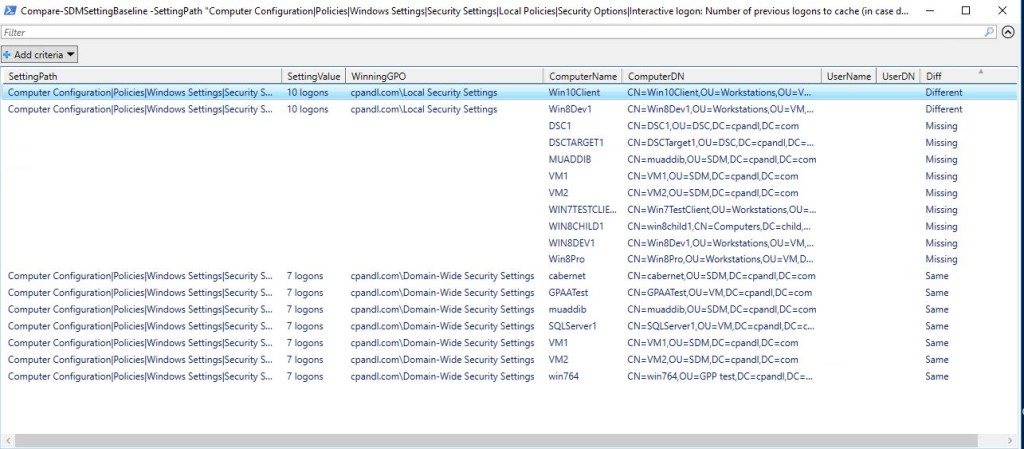
Displaying GPCM baseline comparison results using Out-Gridview
To illustrate how all this works, I’ve recorded a quick video showing the capabilities of GPCM and it’s PowerShell module. Have a look and see how easy it can be to get a quick read-out of how your security hardening is being enforced across your Windows environment:
You can download a trial version of Group Policy Compliance Manager and get started with your own security validations here
Thanks for reading!
Darren



“Have a look and see how easy it can be to get a quick read-out of how *you’re* security hardening is being enforced across your Windows environment”
Your!
Doh! Thanks Robert. Fixed.
Great article as usual. If “your” and “you’re” was worth your time, then I have to mention… “Prove to Me That Critical Security Setting is on Every Machine” isn’t a question.
Should be: Answering the Boss’s Question–“Can You Prove to Me That Critical Security Setting is on Every Machine?”
Great stuff. Thanks
Thanks Matthew. We clearly need more copy editors around here! 🙂