HKEY_CLASSES_ROOTlnkfileshellexIconHandler@
HKEY_CLASSES_ROOTpiffileshellexIconHandler@
Where @ represents the “Default” registry value. Each of these values needs to have no data in them in order for this fix to work (and you’ll need to restart the target machine).
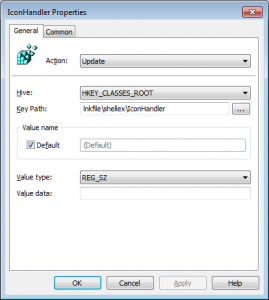
The GP Preferences items were very easy to craft. The following screenshot shows an example of the one I did for the lnk files:
Note that the value data field is left blank. That, in combination with using the “Update” action on the GP Preferences item, makes it easy to blank out a registry value. I then repeated this same process for the piffile path in the registry. Since I created this policy under “Computer Configuration”, I targeted the GPO to my computer objects in AD by linking it to an OU containing my computers. During the next policy refresh, the fix applied and I was protected. When an update is provided by Microsoft, you can again use GP Preferences registry extension to update the registry value with its previous, default value, which is “{00021401-0000-0000-C000-000000000046}” for both lnkfile and piffile.
Cool! GP Preferences strikes again!
Darren